The Human Factors in Security Breaches
Most companies that we come across in our line of work understand the importance of securing their network, so they spend lots of money on setting up firewalls, antivirus software, encryption, etc. But the truth is that if cybercriminals can’t hack their way into your network, they have another trick up their sleeves. It’s called social engineering.
What is Social Engineering?
Hackers manipulate you into divulging personal information, financial information, or login credentials. They then use it to get past all those firewalls and controls that you spent so much money putting in place. In fact, statistics show that 98% of cyberattacks involve social engineering.
Phishing
The most common social engineering attacks is known as phishing. A social engineer sends you an email pretending to be a prospective customer, your IT, or even your boss and asks you to send them information or money, download a malicious file, or click on a malicious link that they provide.
Sample Phishing Email
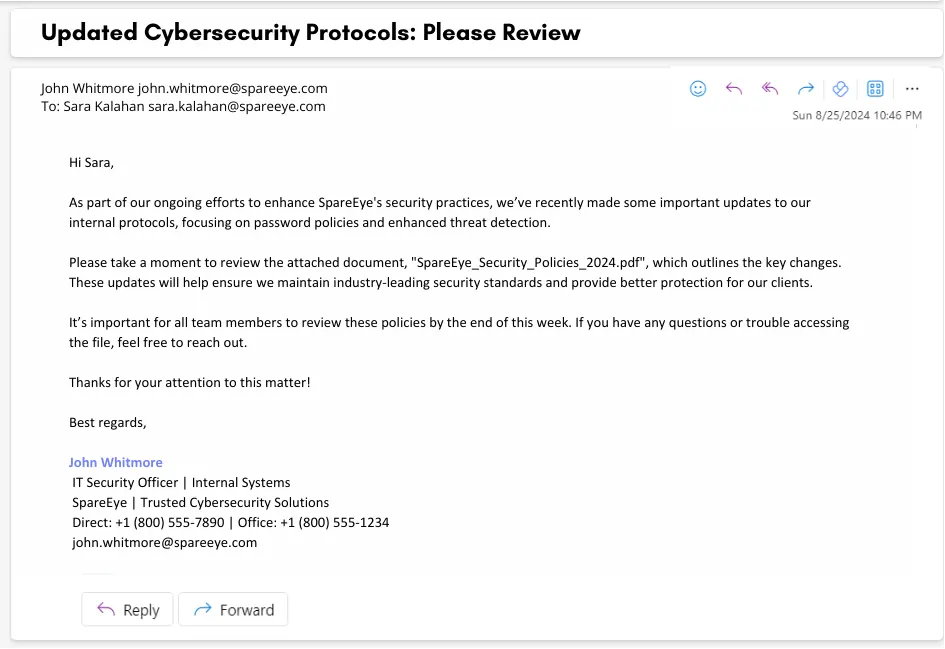
Phishing attacks are so common, they account for nearly 1.2% of all emails sent. That’s 3.4 billion phishing emails daily! I’m sure that you have caught a good number of them yourself.
The trouble is that because they happen so often, your spam filter might catch 95% of them, but eventually an employee might click on one. One click may seem harmless, but that’s all that is needed for malware to be installed on your system or for credentials to be compromised.
Successful Social Engineering Attempts
A few years back, Google and Facebook lost $100 million due to a phishing attack. The attacker pretended to be a Taiwanese supplier called Quanta that both companies use, and sent fake invoices, which Google and Facebook paid up.
In 2020, U.S. healthcare provider Elara Caring was compromised due to a phishing attack that targeted two of its employees. Attackers gained access to the PHI of over 100,000 patients, including social security numbers, driver’s license numbers, banking information, names, and birthdays. The unauthorized access was only detected after a whole week had passed.
Well, it seems quite hopeless. If no technical control can completely remove the risk of human error, what is there left to do to prevent social engineering attacks?
Security Awareness Training
You can actually do plenty. At SpareEye we offer our clients phishing simulations where we assess their employees’ susceptibility to phishing emails, and biannual security awareness training, where we educate them on the relevant cyber risks and how to stay safe online. Security training works. 80% of organizations report that security awareness training has reduced the risk of their employees falling for phishing attacks. But not all trainings are created equal. The training won’t be effective if your employees aren’t paying attention or if it doesn’t cover the right topics.
Here’s how to make sure your company’s security awareness training is effective.
Five Tips for an Effective Security Awareness and Training Program
Keep It Short
The latest statistics show that the average adult attention span is 8.5 seconds. No one has the time or patience to sit for hours learning anything, especially when they have a job to do and tasks to accomplish. Additionally, long trainings can overwhelm employees, reducing retention. Keep the length of your training to under 30 minutes to maintain attention and maximize effectiveness.
Engage The Audience
Even with shorter trainings, lecturing for a half hour straight will lose your audience. Instead, create opportunities for interaction to keep participants engaged. Involve the audience by asking questions and encouraging them to share real world examples. Invite them to ask questions throughout the session to clarify points or address concerns. When people actively participate, they are more likely to understand and remember what they learn.
Another idea to make the training more interactive is to make it a live class instead of a video or zoom class. From our experience, most people keep their cameras off during zoom trainings and participate less. It is much easier to gauge the attentiveness of your employees when you can see their body language and control the number of distractions that are around them.
It’s a good practice to conduct phishing simulations in the weeks before the training, as knowing that they clicked on a phishing email (even though it was fake) can spur your employees to pay better attention during the training.
Keep It Relevant
Tailor the content to your specific audience. Don’t waste time discussing topics irrelevant to their role. Use real-life examples that employees are likely to encounter and update these examples frequently to stay current with emerging threats.
Keep It Simple
Avoid using overly technical language that may confuse or intimidate your audience. The goal is to ensure that every employee walks away with a clear understanding of how they can contribute to the company’s cybersecurity. Focus on actionable tips and steps they can implement immediately.
Don’t Be Overbearing
People don’t like to be made to feel stupid. Don’t overstress the fact that most breaches are the result of human error, instead, empower them by emphasizing how they can play a key role in preventing breaches. Positive reinforcement can help build confidence and motivate employees to apply what they’ve learned. Show them how their actions can make a difference and offer guidance without placing undue pressure on them.
Key topics to cover:
When developing your cybersecurity training, focus on key areas employees should understand:
Email Security
Explain how to identify and handle spam emails, phishing attempts, and suspicious attachments. Teach employees to read links carefully before clicking, checking for strange domain names or subtle changes in common URLs.
Passwords
Discuss best practices for password creation, including using long, complex, and unique passwords. Encourage the use of password managers for safe storage and emphasize the importance of not sharing passwords.
Safe Internet Browsing
While most people think it’s easy to tell the difference between a real website and a fake one, that isn’t the case. 50% of phishing websites are https and making a replica of a web page can be done with just a few clicks. It is important to teach employees to be cautious when clicking links and show them how to find out where the link leads.
Social Engineering
Explain the common tactics used in social engineering, such as impersonation and manipulation. Provide examples of how attackers may use psychological tricks to gain sensitive information and train employees on how to recognize and respond to these threats.
Malware
Teach employees about different types of malware (e.g., viruses, ransomware, spyware) and how to avoid downloading malicious software. Cover best practices for scanning downloads and the importance of keeping software updated.
Remote Working
With more employees working remotely, it’s critical to provide extra security measures for home offices. Educate them on securing home networks, using VPNs, and being cautious about what devices connect to their work systems.




